Kaspersky foils more than 200M attempts to exploit remote admin tool in Southeast Asia last year
In mid-March of last year, the World Health Organization (WHO) officially declared the world was facing a pandemic, and countries rushed to enact measures to stem the spread. A popular measure to combat the pandemic was switching companies to remote work. However, with little time to make the transition, many companies had no time to enact proper security measures, leaving them vulnerable to a number of new security risks. One of the most common were attacks against the protocols used by employees to access corporate resources remotely.
RDP is perhaps the most popular remote desktop protocol and is used to access Windows workstations or servers. After the switch to remote work, bruteforce attacks against this protocol skyrocketed. In a bruteforce attack, attackers test different usernames and passwords until the correct combination is found—and they gain access to the corporate resources.
Over the past year, while the total number of bruteforce attacks has ebbed and flowed, they have continued to increase when compared to pre-pandemic levels.
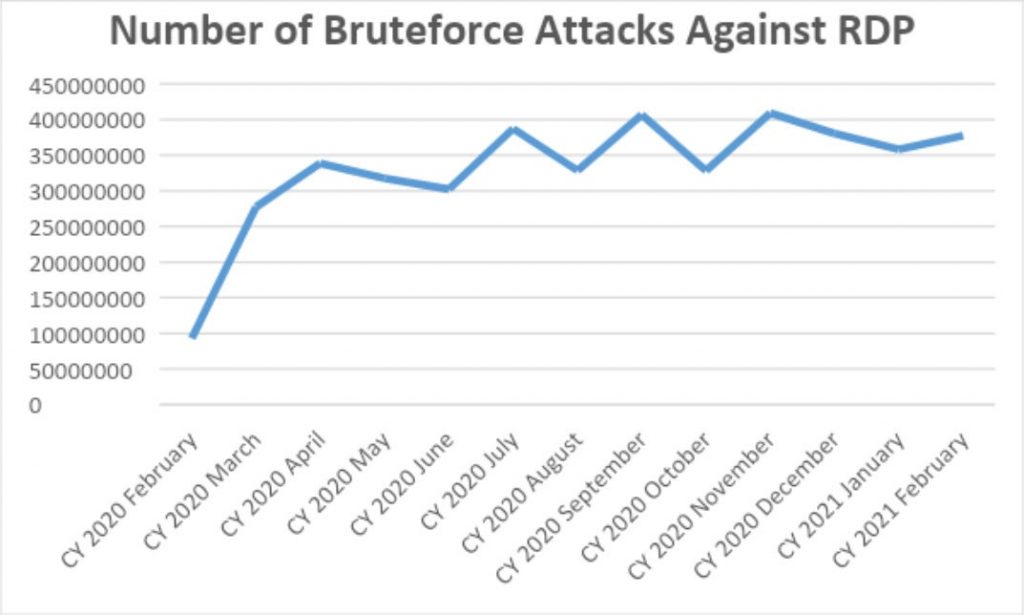
Total number of bruteforce attacks against RDP from February 2020-February 2021
According to Kaspersky’s telemetry, when the world went into lockdown in March 2020, the total number of bruteforce attacks against RDP jumped from 93.1 mln worldwide in February 2020 to 277.4 mln 2020 in March—a 197 percent increase. From April 2020 onward, monthly attacks never dipped below 300 million, and they reached a new high of 409 million attacks worldwide in November.
In February 2021—nearly one year from the start of the pandemic—there were 377.5 mln brute-force attacks—a far cry from the 93.1 mln witnessed at the beginning of 2020.
“Remote work isn’t going anywhere. Even as companies begin considering re-opening their workplaces, many have stated that they will continue to include remote work in their operating model or pursue a hybrid format. That means it’s likely these types of attacks against remote desktop protocols will continue to occur at a rather high rate. 2020 made it clear that companies need to update their security infrastructure, and a good place to start is providing stronger protection for their RDP access,” comments Dmitry Galov, security expert at Kaspersky.
Nearly 600,000 RDP attacks per day targeted remote workers in Southeast Asia
Southeast Asia (SEA) was among the first regions battered by the COVID-19 pandemic. Thailand recorded the first case outside China on January 13, 2020. With little known facts about the virus, nations across the region vigilantly observed and tailor-fitted their restrictions and precautionary measures before the pandemic status was declared by the WHO March last year.
As with the rest of the world, SEA countries then implemented strict measures and border controls a year ago. This forced enterprises and organizations to shift to remote work, learning, and more. In turn, inviting the attention of cybercriminals.
Kaspersky’s telemetry showed a trend — a slow but steady increase in the number of attacks against RDP being used in the region, hitting the highest in the month of September 2020 with 31,019,009 brute force attacks. Overall, the global cybersecurity company blocked a total of 214,054,408 RDP exploits in SEA.
In the Philippines, the highest number of attempted attacks against RDP was recorded in August 2020 (1,306,318). A total of 6,979,713 attacks against RDP in the country were blocked by Kaspersky in 2020.
“On a daily average, our solutions foiled almost 600,000 RDP brute force attacks here in Southeast Asia last year. Our latest numbers also showed that cybercriminals are not interested in taking a break. In the first two months of 2021, we’ve already detected more than 65 million attempts to exploit this remote working tool which is 30% of 2020’s total incidents,” says Chris Connell, Managing Director for Asia Pacific at Kaspersky.
“The sheer number of attacks we’ve identified and we continue to monitor paints a worrying picture of the increasing vulnerability employees working from home are exposed to. The pandemic’s second and third waves are still happening, unfortunately, so we see that remote work is here to stay at least for a long while. We call on business owners, from the largest enterprises to small and medium businesses, to consider putting up basic endpoint solutions and utilize adaptive training to repel these malicious attempts online,” he adds.
Understanding the financial challenges being faced by SMBs in SEA, Kaspersky currently gives discounts for its latest Kaspersky Endpoint Detection and Response Optimum (KEDRO) solution.
The promo for this comprehensive tool stands for new and existing customers valid on 10-999 nodes across the region until June 30, 2021. Customers can get up to 33% in savings for a 1-year license, and up to 40% for three years.
Interested SMB owners can find out more about this promo at https://go.kaspersky.com/Kaspersky_EDRO_SEA_Promotion.html.
Read more about the biggest evolutions in the threat landscape since the pandemic began on Securelist.
To keep your company safe from bruteforce attacks, Kaspersky experts recommend:
- Enable access to RDP through a corporate VPN
- Enable use of Network Level Authentication (NLA) when connecting remotely.
- If possible, enable multi-factor authentication
- Use corporate security solution empowered with network threat protection such as Kaspersky Endpoint Security for Business
About Kaspersky
Kaspersky is a global cybersecurity company founded in 1997. Kaspersky’s deep threat intelligence and security expertise is constantly transforming into innovative security solutions and services to protect businesses, critical infrastructure, governments and consumers around the globe. The company’s comprehensive security portfolio includes leading endpoint protection and a number of specialized security solutions and services to fight sophisticated and evolving digital threats. Over 400 million users are protected by Kaspersky technologies and we help 250,000 corporate clients protect what matters most to them. Learn more at www.kaspersky.com.