Employees hastily placed on remote work setup kept most of Southeast Asia’s businesses afloat when the pandemic hit in 2020. Unfortunately, it was also remote work that caused some headache for companies that were struck with RDP attacks, which are not even going away soon, according to Kaspersky.
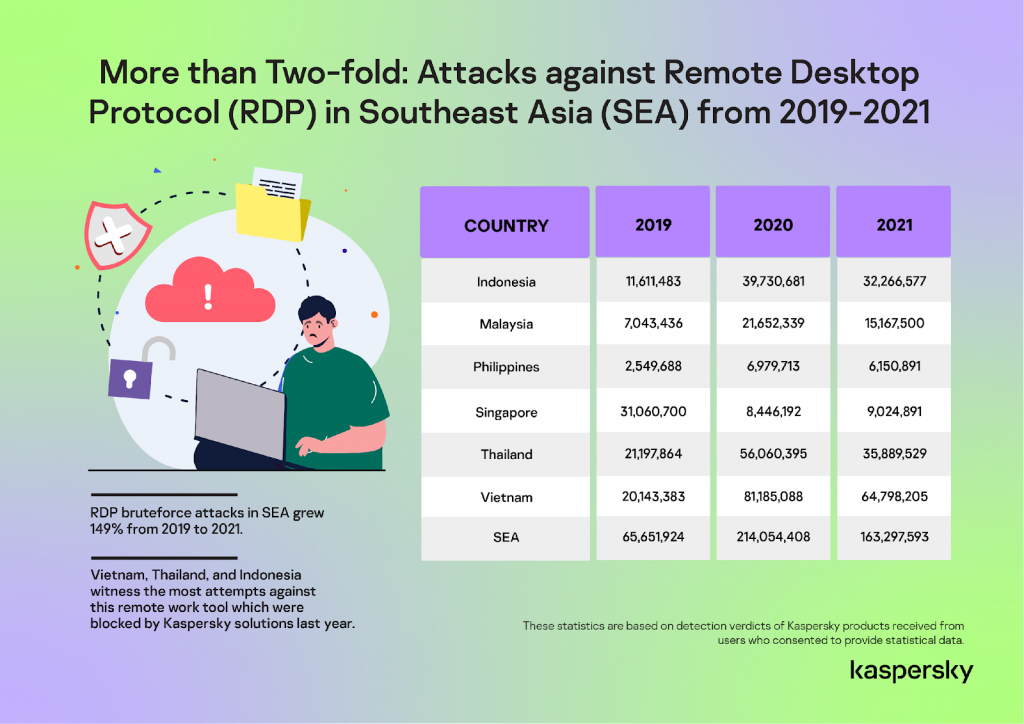
Data from the cybersecurity company showed remote desktop protocol (RDP) attack attempts among Kaspersky users in Southeast Asia increased by 149% from 2019 to 2021. The RDP attacks recorded in the region was only 65,651,924 in 2019 but ballooned to 214,054,408 in 2020 when most of the region’s workforce were forced to temporarily leave their offices to work from their homes full-time.
In 2021 when employees were given the flexibility to work back on-site and remotely, RPD attacks attempts in SEA declined by an average of 20% compared to 2020 but the numbers are still higher than in 2019. RDP attack attempts in Singapore even grew by 6.85% in 2021 compared to 2020.
But what exactly is RDP?
RDP or remote desk protocol is Microsoft’s proprietary protocol that enables a user to connect to another computer through a network of computers running Windows.
RDP is widely used by both system administrators and less-technical users to control servers and other PCs remotely but this tool is also what intruders exploit to penetrate the target computer that usually houses important corporate resources. Microsoft 365 remains the preferred productivity software in the business sphere, followed by Google Workspace.
When devices are outside the company’s local network, away from the protection of the IT department, confidential information will always have a huge potential to be stolen or lost due to carelessness.
With the first wave of lockdowns, computers that have been hurriedly made available to remote workers were incorrectly configured. This scenario provided an opportunity for cybercriminals to launch attacks, particularly using brute-force attack attempts (systematically trying to find the correct username-password pair) to successfully get remote access to the target computer in the network.
“The experience during the pandemic has put forth a collective clamor all over the world to shift to a hybrid work setup. Sectors such as finance, information, management, and professional services have shown to benefit from working and collaborating remotely,” says Yeo Siang Tiong, general manager for Southeast Asia at Kaspersky.
“The hike in RDP attacks during this period is not unique to the SEA region. Globally, this type of threat rose 120% from 2019 to 2021. Given that remote work is here to stay, we urge companies to seriously look into securing their remote and hybrid workforce to protect their data,” he said.
How to stay safe?
Kaspersky experts foresee that attacks on remote-access infrastructure (as well as collaboration tools) are unlikely to stop any time soon. So if you currently use RDP in your work, Kaspersky experts advise to take all possible protection measures, such as:
- Use different strong passwords to access different corporate resources
- Update all software and apps on employee devices to the latest version
- Enable access to your network or make RDP available only through a corporate VPN
- Use Network Level Authentication (NLA)
- If possible, enable multi-factor authentication
- If you don’t use RDP, disable it and close port 3389
- Give employees basic security awareness training which can be done online. Kaspersky and Area9 Lyceum have a free course to help staff work safely from home
- Ensure your employees are equipped to securely work from home and know who to contact when faced with an IT issue
- Use a reliable corporate security solution that will be installed on all employee devices, as well as solutions for tracking equipment in case of loss. Choose one with network threat protection such as Kaspersky Integrated Endpoint Security that includes log inspection functionality to configure monitoring and alert rules for brute force and failed login attempts
- Where possible, use encryption on devices used for work purposes
- Ensure access to the latest threat intelligence to boost your protection solution. For example, Kaspersky offers a free COVID-19-related threat data feed
- Make backup copies of critical data
To help companies build their cybersecurity capacity, Kaspersky is offering its Endpoint Detection and Response Optimum at 35% off. Interested companies can visit this link to know more.
Read Kaspersky’s full 2021 Threat Landscape Report for Southeast Asia here https://kasperskysea.co/premium_report.
About Kaspersky
Kaspersky is a global cybersecurity and digital privacy company founded in 1997. Kaspersky’s deep threat intelligence and security expertise is constantly transforming into innovative security solutions and services to protect businesses, critical infrastructure, governments and consumers around the globe. The company’s comprehensive security portfolio includes leading endpoint protection and a number of specialized security solutions and services to fight sophisticated and evolving digital threats. Over 400 million users are protected by Kaspersky technologies and we help 240,000 corporate clients protect what matters most to them. Learn more at www.kaspersky.com.
very informative