Kaspersky reports on cybercriminal activity on the Darknet market in the region
According to Kaspersky’s Digital Footprint Intelligence (DFI) report for APAC, database leaks in the region account for 95% of the total amount of advertisements. Singapore’s and Australia’s data leaks market are by far the largest when looking at the weighted GDP amounts of orders.
The report highlights results collected last year for organizations and even countries to keep an eye on possible external threats and stay informed about potential cybercriminal activities, including ones being discussed on the Darknet.
Monitoring of external data sources in Kaspersky’s Digital Footprint Intelligence service, including Darknet resources, provides insights into cybercriminal activity through different stages of attack lifecycle. In the second part of the report, the company presents Darknet analysis results.
There are two major types of data found when analyzing an organization’s digital footprint: fraudulent activities and cyberattack footprints. While Kaspersky discovered numerous fraud signs, the focus in the report remains on attack detection.
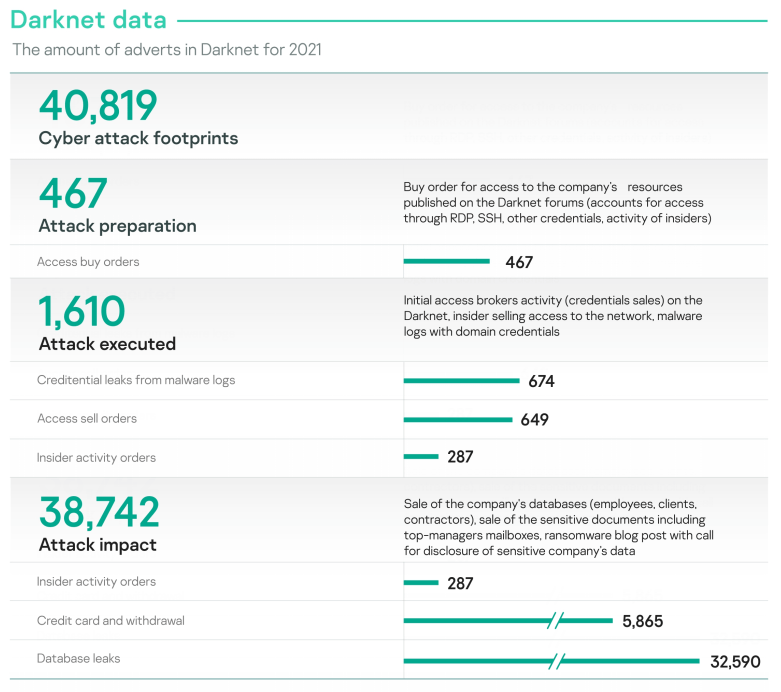
Figure 1: The amount of adverts in Darknet for 2021 – cyberattack footprints
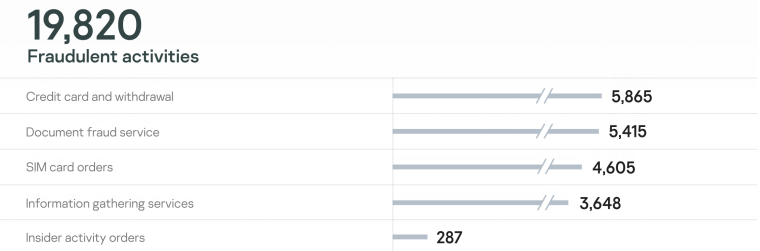
Figure 2: The amount of adverts in Darknet for 2021 – fraudulent activities
Darknet activity related to attack impact (advertisements on selling data leaks and compromised data) dominates the statistics as these are spread over time, where criminals sell, resell and repack a lot of data leaks from the past.
Stage 1: Interest to buy access
Cybercriminals who are looking for initial access offers know that there is a large market of such advertisements. Organizations from Australia, India, mainland China, and Pakistan are the major adversaries’ interest to start an attack. These countries were present in 84% of ads from the attack preparation category.
Pakistan and Australia attract huge interest as seen by the number of orders weighted with their GDP.
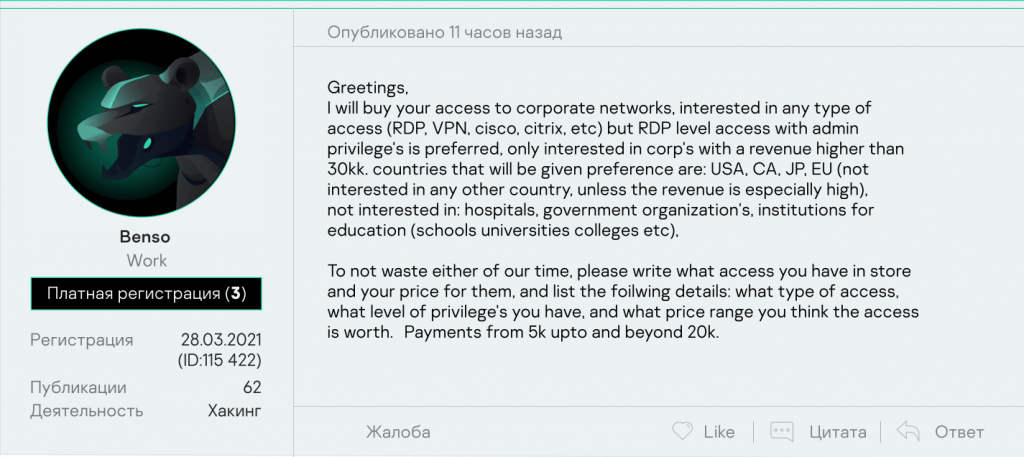
Figure 3: An example of access buy order
Looking at the size of infrastructure, businesses, and industrialization – mainland China poses relatively low interest for adversaries. This may indicate the presence of a language barrier cybercriminal scene in the APAC region or the complications with network-level access to organizations in the country.
Access buy order is a request to buy access to a single or a list of specific organizations or industries in a specific region.
Insider activity buy orders, however, are requests to buy insider services which can lead to credentials or data leaks, source of information gathering service (e.g., PII data exfiltration by request). Those orders are the most inconclusive type of findings for remediation planning.
Stage 2: Orders for access – ready to execute
The most promising findings are from the attack execution stage: artifacts are stating that adversaries have capabilities or already have access to organizations’ networks or services, but there is no business impact yet. In terms of advertisements on the Darknet, indicating an attack executed, Australia, India, mainland China and the Philippines cover 75% of those detected by Kaspersky.
It is divided into three types:
- Initial access brokers – Sell orders for specific organizations, or bulk orders with organizations grouped by industry and/or region.
- Insider activity sell orders – Request to sell insider services that can lead to credentials leak, source of information gathering service (e.g. PII data exfiltration by request), or data leak. The source is usually an insider’s broker.
- Malware logs – Credential stealing malware (stealers) collect credentials into resalable or otherwise accessible data with account usernames and passwords.
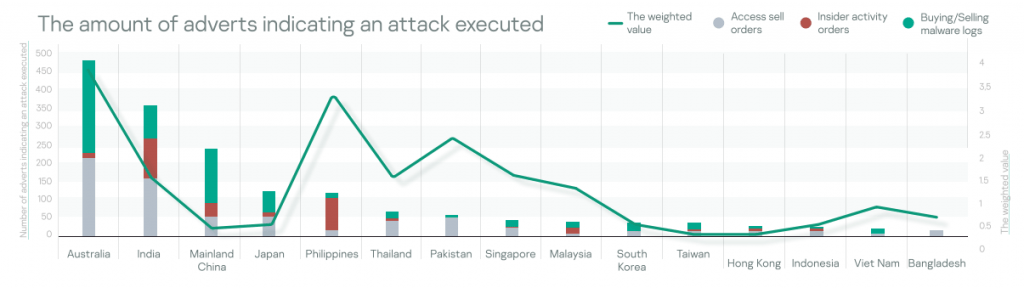
Figure 4: The number of adverts indicating an attack executed
The Philippines, Pakistan, Singapore, Australia, and Thailand organizations are most attacked when weighted with GDP.
The Philippines, India, and mainland China are dominating the insider services market with 82% of orders turnover.
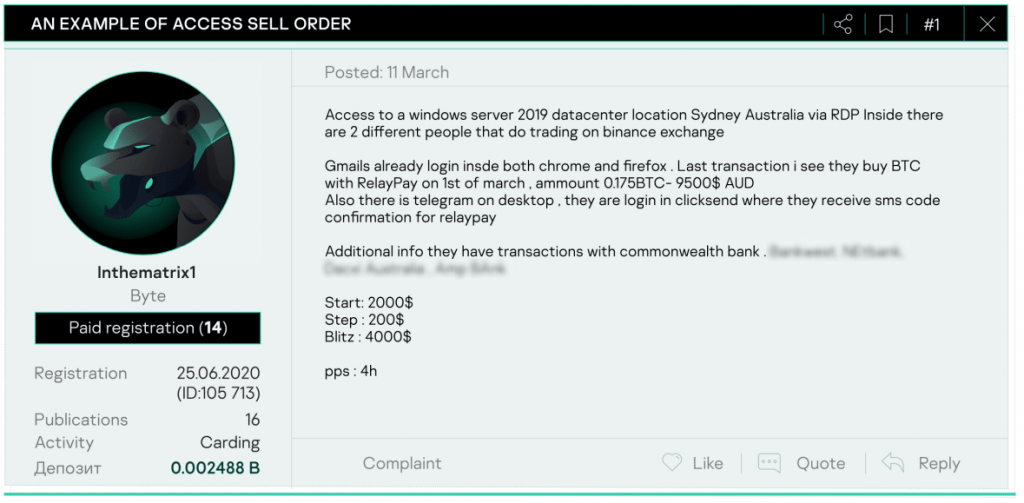
Figure 5 : An example of access buy order
Stage 3: Data leaks and data for sale
Once a data leak occurs, the sale or free access to the stolen information will follow. An indicator of compromise can be data leaks as well as insider activity orders – sale or free access to internal data, including but is not limited to databases, confidential documents, PII, credit cards, VIP information, financial data and many more.
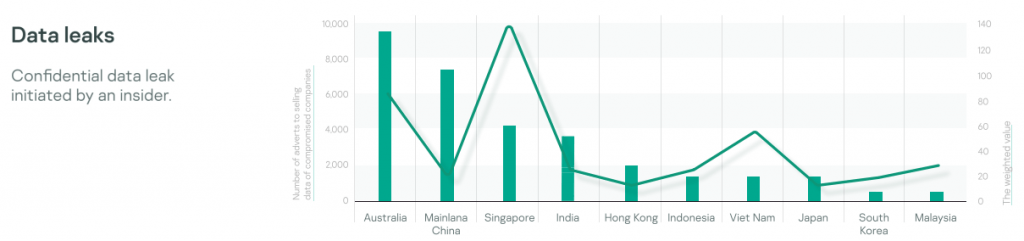
Figure 6: The amount of adverts indicating a compromised system – data leaks1
Organizations from Australia, mainland China, India, and Singapore take 84% of all data leaks sell orders placed on the Darknet.
Singapore’s and Australia’s data leaks market are by far the largest when looking at the weighted with GDP amounts of orders.
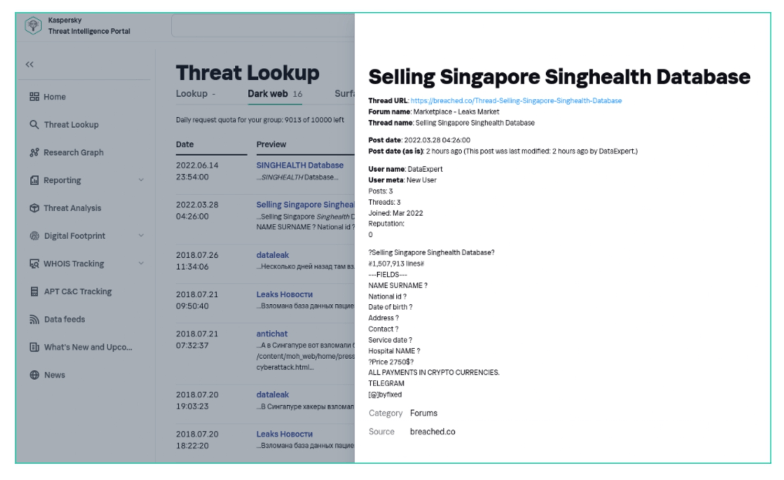
Figure 7: Database selling order example (Source: Kaspersky Threat Intelligence portal)
It should be noted that the Philippines, Pakistan, and Thailand organizations were among the adversaries interest to begin an attack or appeared as already compromised, but the amount of data leaks is on par with other countries from the middle of the group.
“Cybercriminal operations beneath the surface web are clearly busy. From attack preparation and execution, to the impact of a data leak and then selling and reselling of stolen information, this functioning malicious system is a serious threat for businesses and organizations here in APAC,” says Chris Connell, Managing Director for Asia Pacific at Kaspersky.
“Selling data and access to the companies often goes hand in hand. This means a successful attack to your organization can be two pronged. Your confidential information can be stolen and be sold, and these cybercriminals can open and offer your infected system to more malicious groups. A double whammy that requires a proactive defense that includes strong incident response and Darknet monitoring capabilities through real-time and in-depth threat intelligence reports,” he adds.
How to protect your company from these kind of threats
Demand for corporate and personal data on the black market is high, and it doesn’t always involve targeted attacks. Attackers may gain access to the infrastructure of a random company to sell it to blackmailers or other advanced cybercriminals later.
An attack like this can affect a company of any size, big or small, because corporate system access is often priced moderately on underground forums, especially compared to the potential damage to a business.
Sellers on the dark web most often offer remote access via RDP. To protect corporate infrastructure from attacks through remote access and control services, make sure the connection via this protocol is secure by:
- providing access to services (for example, RDP) only through a VPN,
- using strong passwords and Network Level Authentication (NLA),
- using two-factor authentication for all services,
- monitoring for leaks of access data. Dark web monitoring is available on Kaspersky Threat Intelligence Portal.
*The report used GPD from https://data.worldbank.org/indicator/NY.GDP.MKTP.CD?view=chart
About Kaspersky
Kaspersky is a global cybersecurity and digital privacy company founded in 1997. Kaspersky’s deep threat intelligence and security expertise is constantly transforming into innovative security solutions and services to protect businesses, critical infrastructure, governments and consumers around the globe. The company’s comprehensive security portfolio includes leading endpoint protection and a number of specialized security solutions and services to fight sophisticated and evolving digital threats. Over 400 million users are protected by Kaspersky technologies and we help 240,000 corporate clients protect what matters most to them. Learn more at www.kaspersky.com.