
Expertise, good analytics and defense mechanisms are required against advanced cyber attacks. In hybrid environment systems, tools and applications are in cloud and non- cloud premises. The Security admin team might struggle with threat detection and response.
Security analyst / infrastructure management analyst help you to detect, triage, investigate and respond to such potential threats with apt analysis before they impact business. Vulnerability assessment and management as a service can help you with day-to-day operations to experts who provide granular focus of each vulnerability.
Moreover, reputable managed it services providers offer customized security solutions based on your organization’s specific needs and requirements. This will also ensure that your organization is compliant with any necessary security regulations or standards.
Recently, Microsoft has released workaround guidance to address a remote code execution (RCE) vulnerability—CVE-2022-30190, known as “Follina”—affecting the Microsoft Support Diagnostic Tool (MSDT) in Windows. A remote, unauthenticated attacker could exploit this vulnerability to take control of an affected system. Microsoft has reported active exploitation of this vulnerability in the wild.
ref:Microsoft Releases Advisory to Address Critical Remote Code Execution Vulnerability (CVE-2022-26809) | CISA
The defense in fix is incorporated into the cumulative updates for Windows 10 and newer versions. When URL protocol is used for calling MSDT from any application such as word, a remote code vulnerability exists. In this case, an attacker can run arbitrary code with privileges. Microsoft took care of such a vulnerability by introducing software patches in Windows 10 version and higher.
For Windows 7 and 8, You can use the SCCM (system center configuration manager) application to fix the Remote Code Execution Vulnerability.
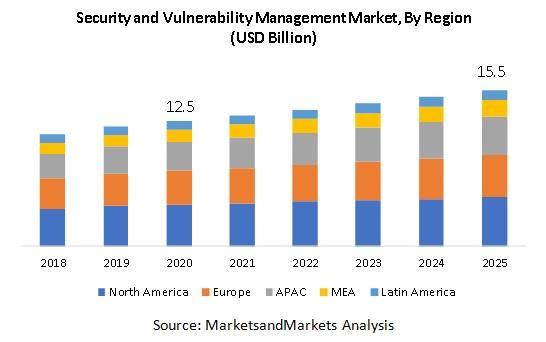
Ref: Security and Vulnerability Management Market Expected to Grow (openpr.com)
The main types of security vulnerabilities based on their more extrinsic weaknesses:
- Porous defense
- Risky resource management
- Insecure interaction between components
A porous defense weakness is one that could allow users to bypass or spoof authentication and authorization processes. Usually, there are many applications like Duo which use authentication processes. The Duo authentication process can be bypassed. There are chances to use the organization resources bypassing the authentication or authorization process. Application is helpful, allowing users to connect users to organization networks remotely; however if the authentication process is bypassed, there can be an issue with data security. There must be a way to trigger an alarm or message if any user working remotely, bypassing the authentication and message should go to their respective IT admins. Managed IT services in India who cater IT security services have majorly focussed on such vulnerabilities, helping in running the production work load smoothly.
Understanding the vulnerabilities and its nature, we have to either schedule timely patches to systems or build a software that automatically fixes any vulnerabilities understanding its pattern. This might take some time as technology is still dependent on the mind of coders/developers. Machine learning/AI is a fix that includes algorithms which can detect/identify the behavior of any program/software. Shaping up the technology according to organization standards needs collaborative efforts. Security Analysts can monitor and help organizations to fix the security vulnerabilities and protect the organization data as well.

Your article on security and vulnerability assessment through managed IT services provides valuable insights into the critical role technology plays in safeguarding businesses. The comprehensive analysis underscores the importance of robust cybersecurity measures. For those interested in exploring managed IT services further, I recommend checking out https://www.cleveroad.com/managed-it-services/ for additional resources and information on how these services can strengthen security protocols.