In February, Kaspersky experts discovered an attack using zero-day vulnerability in the Microsoft Common Log File System (CLFS). A cybercriminal group used an exploit developed for different versions and builds of Windows OS including Windows 11 and attempted to deploy Nokoyawa ransomware. Microsoft assigned CVE-2023-28252 to this vulnerability and patched it recently as part of Patch Tuesday. The threat actor also attempted to execute similar elevation of privilege exploits in attacks on different small and medium-sized businesses in the Middle East and North America, and previously in Asia regions.
While most of the vulnerabilities discovered by Kaspersky are used by APTs, this one turned out to be exploited for cybercrime purposes by a sophisticated group that carries out ransomware attacks. This group stands out by the usage of similar but unique Common Log File System (CLFS) exploits. Kaspersky has seen at least five different exploits of this kind. They were used in attacks on retail and wholesale, energy, manufacturing, healthcare, software development and other industries.
Microsoft assigned CVE-2023-28252 to the discovered zero-day. This is the Common Log File System elevation of privilege vulnerability which gets triggered by the manipulation of file format used by this subsystem. Kaspersky researchers uncovered the vulnerability in February as a result of additional checks into a number of attempts to execute similar elevation of privilege exploits on Microsoft Windows servers belonging to different small and medium-sized businesses in the Middle Eastern and North American regions.
CVE-2023-28252 was first spotted by Kaspersky in an attack where cybercriminals attempted to deploy a newer version of Nokoyawa ransomware. Older variants of this ransomware were just “rebranded” variants of JSWorm ransomware, but in the aforementioned attack the Nokoyawa variant was quite distinct from JSWorm in terms of a codebase.
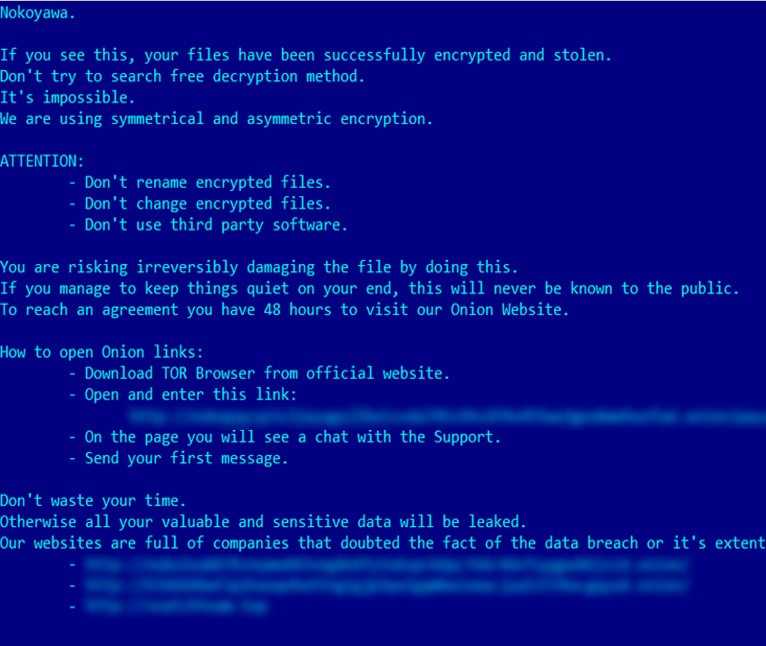
The exploit used in the attack was developed to support different versions and builds of Windows OS including Windows 11. Attackers used CVE-2023-28252 vulnerability to elevate privileges and steal credentials from the Security Account Manager (SAM) database.
“Cybercrime groups are becoming increasingly more sophisticated using zero-day exploits in their attacks. Previously it was primarily a tool of Advanced Persistent Threat actors (APTs), but now cybercriminals have the resources to acquire zero-days and routinely use them in attacks. There are also exploit developers willing to help them and develop exploit after exploit. It’s very important for businesses to download the latest patch from Microsoft as soon as possible, and use other methods of protection, such as EDR solutions,” said Boris Larin, Lead Security Researcher with the Global Research and Analysis Team (GReAT).
Kaspersky products detect and protect against the exploitation of the above vulnerability and related malware.
Learn more about this new zero-day on Securelist. Additional details will be shared nine days after the April Patch Tuesday passes so companies have enough time to patch their systems.
To protect your organization from attacks that exploit the aforementioned vulnerability, Kaspersky experts recommend:
- Update your Microsoft Windows as soon as possible and do so regularly
- Use a reliable endpoint security solution such as Kaspersky Endpoint Security for Business that is powered by exploit prevention, behavior detection and a remediation engine that is able to roll back malicious actions.
- Install anti-APT and EDR solutions, enabling capabilities for threat discovery and detection, investigation, and timely remediation of incidents. Provide your SOC team with access to the latest threat intelligence and regularly upskill them with professional training. All of the above is available within Kaspersky Expert Security framework.
- Along with proper endpoint protection, dedicated services can help against high-profile attacks. The Kaspersky Managed Detection and Response service can help identify and stop attacks in their early stages, before the attackers achieve their goals.
About Kaspersky
Kaspersky is a global cybersecurity and digital privacy company founded in 1997. Kaspersky’s deep threat intelligence and security expertise is constantly transforming into innovative security solutions and services to protect businesses, critical infrastructure, governments and consumers around the globe. The company’s comprehensive security portfolio includes leading endpoint protection and a number of specialized security solutions and services to fight sophisticated and evolving digital threats. Over 400 million users are protected by Kaspersky technologies and we help 240,000 corporate clients protect what matters most to them. Learn more at www.kaspersky.com.