Yeo Siang Tiong, General Manager for Southeast Asia, Kaspersky
A long time ago in the cybersecurity space far far away, the choice of a threat intelligence service was often restricted to a handful of providers. Today, the cybersecurity industry in APAC is worth at least USD 30.45 billion and expected to grow at an annual rate of 18.3% from 2020 to 2025, with multiple cybersecurity vendors seeking a bigger slice of the proverbial pie.
For any chief information security officer (CISO) or IT lead, operating in today’s highly digitalized environment, not only are they tasked with establishing and maintaining the digital transformation efforts of their companies on a tight budget, they must also ensure that the company’s IT policy is compliant with the data protection regimes in the markets that they operate in.
Clearly, it is not an easy task to take, but little things like having the right threat intelligence service can make life easier. We have been hearing a lot about this for several years now. But what is it threat intelligence exactly and what you should be looking for in a threat intelligence service provider?
Turning intelligence into action
Let’s have a quick refresher. Threat intelligence is data collected and analyzed by an organization in order to understand a threat actor’s motives, targets, and attack behavior. It empowers organizations of all shapes and sizes to make faster, more informed security decisions and shifts their cybersecurity posture from reactive to proactive in the fight against breaches and targeted attacks.
I am aware that there are a lot of free threat intelligence if one has a knack on researching. However, let me put it this way. A premium threat intelligence report or feed is like a special block screening of an amazing movie. You get the first dibs of the plot and perhaps get to know the characters even. Eventually, the film will be shown in major cinemas. Then after say, six months or more, it will land on several streaming services.
With us at Kaspersky, we provide comprehensive, real-time, organic, and actionable information on our premium threat reports and data feed which is why they are exclusive to the enterprises and organizations which have subscribed to our services. We see to it that we share such with the law enforcement agencies as well, because cooperation is key to fighting cybercriminals.
After a few months, we will then make such data available in public. Why is it not ideal to wait until the mass release of a threat report? Because it will allow you to act fast, to assess your risks, check your endpoints, fix the loopholes which they may exploit. Because knowing first-hand such critical information can save you money, reputation, and headache. Because proactive security is necessary at this time and age.
You may wonder why don’t we make our findings public to begin with? Let us remember here that public here means anyone – including them, cybercriminals. The last thing we want is to tip them off.
Aside from these, what else should you be looking for in a threat intelligence service provider?
- Check their sources
Threat intelligence should make your systems smarter through data feeds. To get the feeds you need sensors scattered all across the globe to ensure that your data is reflective of the real-time, global threat landscape.
For example, our very own Threat Intelligence portfolio is powered by millions of Kaspersky’s global users who agreed to share their anonymized data. This huge network builds our Kaspersky Security Network (KSN) which collects more than 340,000 malicious files per day, allowing us to get rich information compared with firms with limited sensors and workforce.
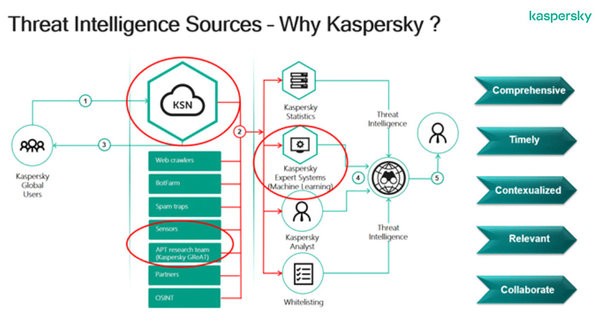
- The data collection strategy needs to be GReAT
Speaking of human force, a threat intelligence service’s data collection strategy should be the most important factor to consider in your evaluation of their capabilities because they can only provide intelligence as far as the parameters of their data sources. Given that cybersecurity attacks are often transnational in nature, it is important that a vendor can source information globally and put pieces of the puzzle together in a way that makes sense for your IT staff. It should not be aggregated, it should be organic. It should also be critically monitored and studied by the brightest minds who can understand tactics, techniques, and procedures (TTPs).
To assess whether a threat intelligence service has such a capability, look at their research team and see what kind of campaigns that they have uncovered. For example, Kaspersky’s Global Research & Analysis Team (GReAT) found that the Lazarus APT group shifted their modus operandi to launch targeted ransomware attacks against businesses in Asia, extending as far as France in Q2 this year.
- Check the visibility
I have already mentioned the borderless nature of cyberthreats. Hence the visibility of your provider should be another box you have to tick. Look into their Advanced Persistent Threat (APT) logbook and their database. Are they monitoring cyberthreats only from a particular country or region? Or do they have a global reach? Are there researchers only based in one country? Or do they have a network of experts scattered around the world? The answers for these questions are essential.
- The provider should understand the difference between intelligence and data
At the heart of the debate between intelligence and data lies the concept of context. Assuming now you’ve got your data sources setup and information is feeding in from all corners of the globe, but you’re asking yourself the million dollar question: how do I know what is important and why is it important?
Things such as threat names, timestamps, resolved IPs addresses of infected web resources are useless on their own if they are not enriched with actionable context. When a relationship context is established, the data can be used more readily to answer the questions of “who”, “what”, “where”, “questions”. It is only at this point that data becomes the finished article – intelligence – and you now receive a boost to incident investigation, as well as uncover new Indicators of Compromise (IoC) in your IT network.
- The ability to integrate is key
Integration can be a dirty word of the IT industry. With constant technological upgrades and the evolution of standards happening all the time, the ability to integrate new processes into existing IT operations is a never-ending challenge.
Similarly, for threat intelligence, it is important that your service provider can provide delivery methods, integration mechanisms and formats that support smooth integration of threat intelligence into your existing security controls.
The endgame
The above-mentioned tips are just a few of the many other aspects you should consider when looking for a threat intelligence service, but they serve as a good stepping stone in bolstering your cybersecurity posture for now. With threats becoming increasingly complex and malicious, having the latest enterprise security programs are no longer sufficient. Adding threat intelligence to your arsenal of cybersecurity countermeasures will allow you to bring the fight to them.
About Kaspersky
Kaspersky is a global cybersecurity company founded in 1997. Kaspersky’s deep threat intelligence and security expertise is constantly transforming into innovative security solutions and services to protect businesses, critical infrastructure, governments and consumers around the globe. The company’s comprehensive security portfolio includes leading endpoint protection and a number of specialized security solutions and services to fight sophisticated and evolving digital threats. Over 400 million users are protected by Kaspersky technologies and we help 250,000 corporate clients protect what matters most to them. Learn more at www.kaspersky.com.
