During Q2 2022, Distributed Denial of Service (DDoS) attacks reached a new level as the share of smart attacks and average duration saw steep increases. Compared to the previous year, the average duration of a DDoS attack rose 100 times, reaching 3,000 minutes. The share of smart attacks almost broke the four-year record, accounting for nearly 50% of the total. Experts also expect an increase in overall DDoS activity, especially with the recent collapse of cryptocurrency. These and other findings are part of a quarterly DDoS report issued by Kaspersky.

A Distributed Denial of Service (DDoS) attack is designed to hinder the normal functioning of a website or crash it completely. During an attack (which usually targets government institutions, retail or financial companies, media or other organizations) the victim loses customers due to the unavailability of their website and their reputation suffers.
From quantity to quality
Compared to figures from Q2 2021, Kaspersky’s solutions defended its users against approximately 2.5 times more DDoS attacks. At the same time, in contrast to the beginning of the year with its dramatic surge in attacks due to hacktivist activity, absolute numbers decreased in Q2 2022. However, this does not mean that the DDoS market has cooled down, instead attacks have changed in quality, becoming longer and more complicated.
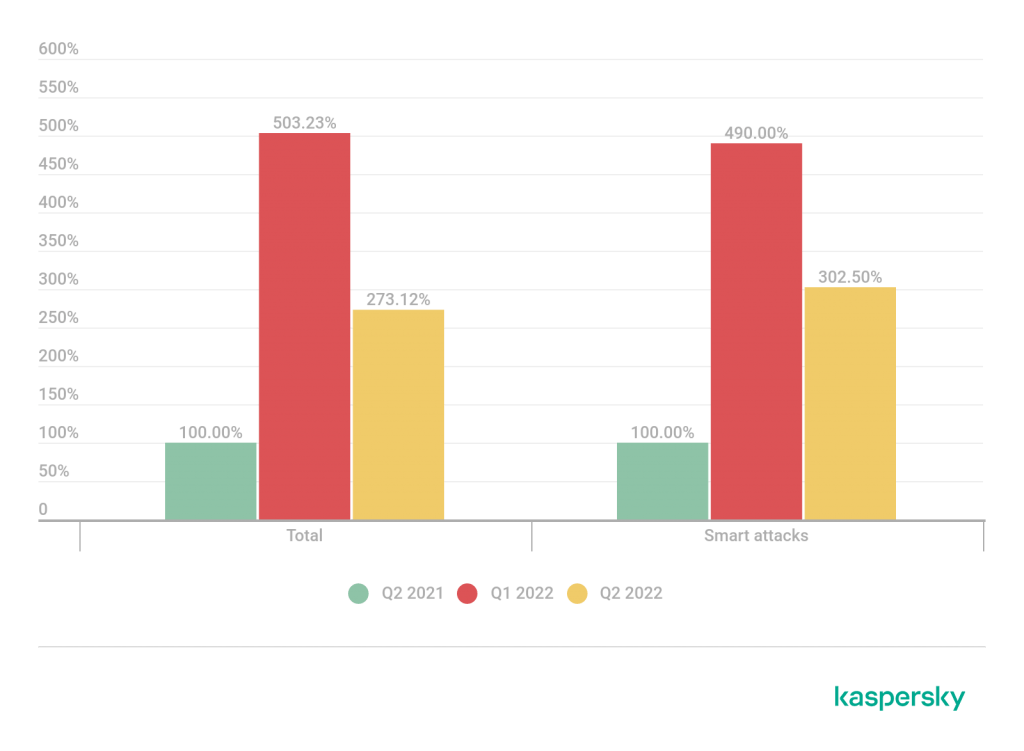
A comparative number of DDoS attacks: Q2 2022 and Q2 2021 as well as Q1 2022.
Data for Q2 2021 is taken as 100%
Average DDoS session lasted 100 times longer
The average duration of an attack in Q2 2022 was 3,000 minutes, or two days. It’s 100 times longer than in Q2 2021, when an attack lasted just for 30 minutes on average. Compared to Q1 2022, which was marked with unprecedented durations for DDoS sessions as the result of hacktivist activity, the Q2 figure also shows an increase – by three times.
Some of the attacks in the past quarter lasted for days or even weeks. A record was set by an attack with a duration of 41,441 minutes, which is just a little less than 29 days.
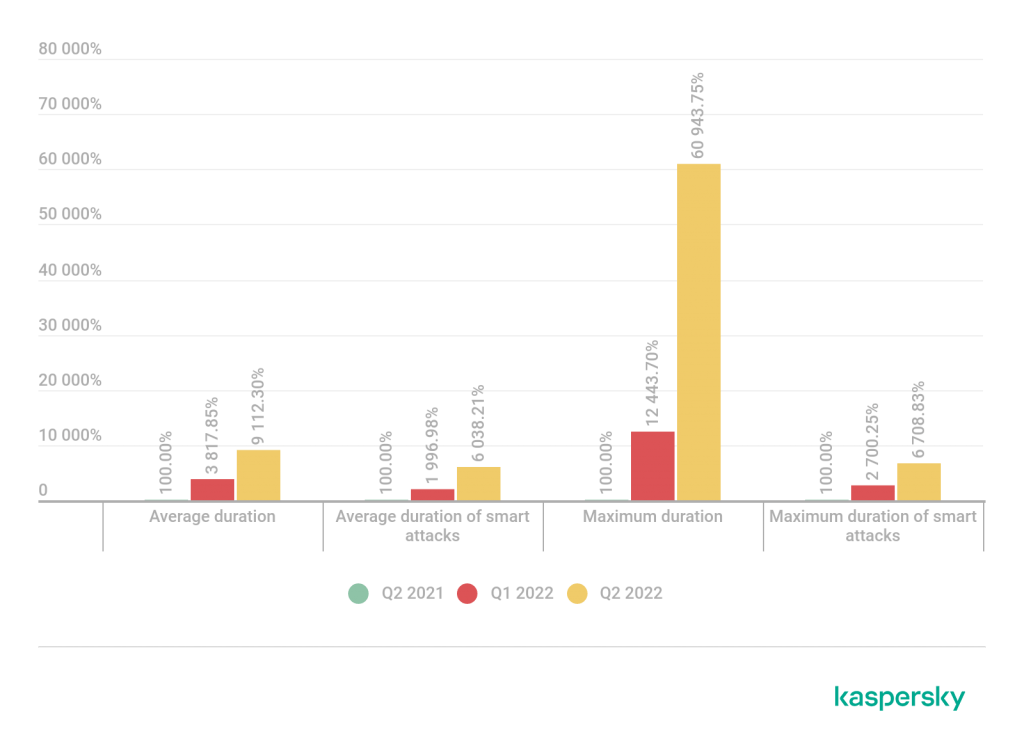
A comparative duration of DDoS attacks: Q2 2022 and Q2 2021 as well as Q1 2022.
Data for Q2 2021 is taken as 100%
“It is extremely expensive to continue an attack for such a long time, especially if it is ineffective due to being filtered by protection solutions. When bots are constantly active, the risk of botnet wear-off, node failure or control center detection increases. The extreme duration of these attacks and the growth in the number of smart and targeted DDoS attacks makes us wonder about the capabilities, professional affiliation and funding sources of the organizers,” comments Alexander Gutnikov, a security expert at Kaspersky.
Smart attacks strive for records
Every second attack in Q2 2022 detected by Kaspersky’s products was smart, meaning its organizers conducted rather sophisticated preparation. The share of smart attacks reached almost 50% in this quarter, which was nearly a new record. The all-time highest share was set four years ago when the DDoS market was in a slump, and it’s unexpected to observe figures that high during a “heated” year in terms of DDoS activity.
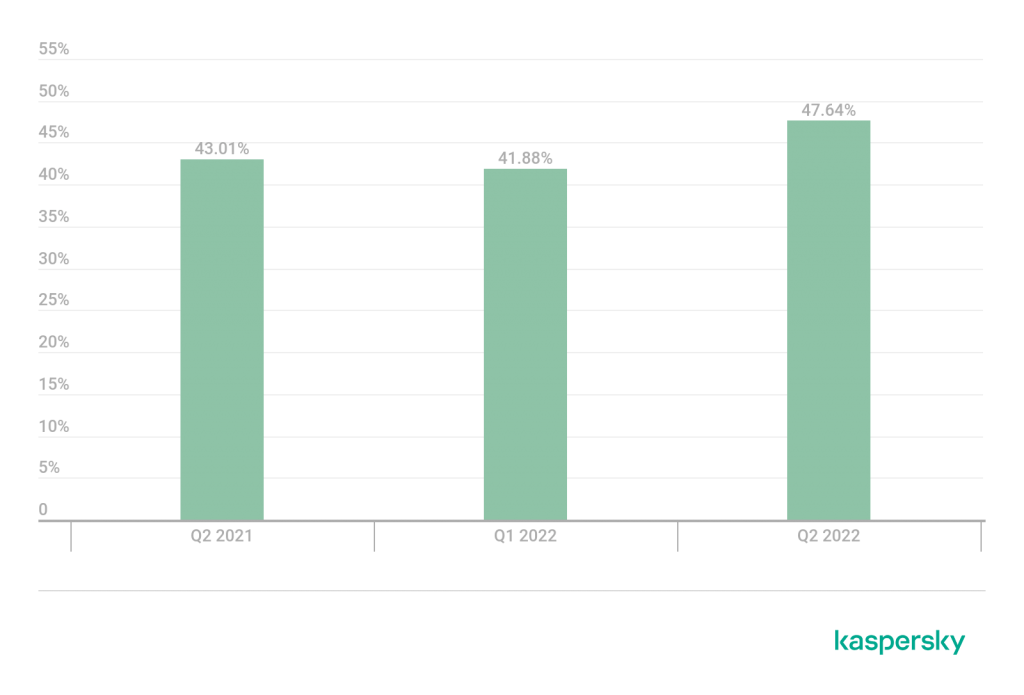
The share of the smart DDoS attacks: Q2 2022, Q2 2021 and Q1 2022
What does the DDoS market have to do with cryptocurrency?
In terms of the number of DDoS attacks, the second quarter was quieter than the first. This is a common phenomenon: the experts usually see a decline in DDoS activity as summer nears. According to the Kaspersky DDoS Intelligence system, this year the dynamics of the number of DDoS attacks within the quarter didn’t match this typical pattern. After a slowdown at the end of Q1, botnet activity steadily grew throughout Q2, resulting in more activity in June than in April. This is consistent with the decline of cryptocurrency, which usually stimulates the heating of the DDoS market.
“The collapse of cryptocurrencies began with the plummet of the Terra (Luna) and has only been gaining momentum since. Various factors indicate that the tendency may continue: for example, cryptominers are selling off farms at low prices to gamers. This can lead to a surge in global DDoS activity,” Gutnikov explains.
Read more about DDoS attacks in Q2 2022 on Securelist.
To stay protected against DDoS attacks, Kaspersky’s experts recommend implementing the following measures:
- Maintain web resource operations by assigning specialists who understand how to respond to DDoS attacks.
- Validate third-party agreements and contact information, including those made with internet service providers. This helps teams quickly access agreements in case of an attack.
- Implement professional solutions to safeguard your organization against DDoS attacks. For example, Kaspersky DDoS Protection combines Kaspersky’s extensive expertise in combating cyberthreats and the company’s unique in-house solutions.
- Know your traffic. Use network and application monitoring tools to identify traffic trends and tendencies. By understanding your company’s typical traffic patterns and characteristics, you can establish a baseline to more easily identify unusual activity that is symptomatic of a DDoS attack.
- Have a restrictive Plan B defensive posture ready to go. Be in a position to rapidly restore business-critical services in the face of a DDoS attack.
About Kaspersky
Kaspersky is a global cybersecurity and digital privacy company founded in 1997. Kaspersky’s deep threat intelligence and security expertise is constantly transforming into innovative security solutions and services to protect businesses, critical infrastructure, governments and consumers around the globe. The company’s comprehensive security portfolio includes leading endpoint protection and a number of specialized security solutions and services to fight sophisticated and evolving digital threats. Over 400 million users are protected by Kaspersky technologies and we help 240,000 corporate clients protect what matters most to them. Learn more at www.kaspersky.com.